IT and tech industry groups applaud passage of semiconductor CHIPS Act
A bipartisan bill intended to boost domestic semiconductor manufacturing and help the U.S. compete with China in the development of cutting edge technologies has passed the House and Senate and will soon become law.
The legislation, known as “CHIPS and Science Act,” passed 243-187 in the House Thursday, and includes approximately $52 billion in government subsidies for U.S. semiconductor production. It also includes $24 billion in investment tax credits for chip plants and other funding to spur innovation and research of other key U.S. technologies.
The IT industry and those that rely on it are expected to benefit significantly from the bill thanks to the increased investments and future growth.
“By investing in the domestic semiconductor ecosystem, the measure will create jobs, boost manufacturing, and spur new businesses in communities around the country, ensuring that the benefits are broadly shared across the United States,” said Jason Oxman, Information Technology Industry Council’s (ITI) President and CEO.
“Our industry will continue to partner with the U.S. government and communities across the country as the measure is implemented,” Oxman added in a press release.
Alliance for Digital Innovation Executive Director Ross Nodurft said: “ADI supports the passage of the bill. ADI is very supportive of the NIST reauthorization portion of the legislation.” He added: “It authorizes the resources that NIST needs to develop standards and guidance that agencies will need to adopt new and modern technologies like cloud and quantum computing, digital identity, cybersecurity and artificial intelligence.”
The bill authorizes a total of $9 billion in funding for the National Institute of Standards and Technology to conduct research and to develop standards for an array of future industries and technologies.
The bill, which President Joe Biden is expected to sign into law later this week, could significantly affect the federal government’s IT components supply chain along with domestic manufacturing supply chain security that is monitored by the National Institute of Standards and Technology (NIST).
IT giants and major federal government contractors like IBM are anticipating using funds from the legislation to boost growth in the sector from semiconductors.
“Our company along with many others is ready to get to work to make sure this investment accelerates U.S. leadership in semiconductor innovation and manufacturing and benefits as many Americans as possible, as soon as possible,” Arvind Krishna, IBM Chairman and CEO said in a statement.
Semiconductors, which are essential and expensive components of modern-day technology ranging from cell phones to sophisticated military systems, have seen an explosion in demand in the past decade. Supply chain issues resulting from the pandemic have contributed to a global shortage of the component.
Watchdog calls on US Courts to establish IT workforce recruiting strategy
The Government Accountability Office in a new report has called on the Administrative Office of the U.S. Courts to create an IT workforce recruitment strategy.
In an analysis published Thursday, the watchdog expressed concern that the court system’s administrative arm is lagging behind on recruiting technology expertise and improving the skills of its existing IT workforce.
“[A]lthough the office identified gaps in the cybersecurity skills of its IT workforce, it did not have a recruiting strategy for IT staff and did not establish a training program for its IT staff,” GAO said. “Fully addressing practices in these areas would help ensure that it has the knowledge and skills to tackle pressing IT issues.”
In addition to recruitment and upskilling, GAO said that appointing a chief information officer with enterprise-wide authority could address IT oversight and guidance shortcomings.
Currently, the U.S. court system’s administrative office does not have a CIO, and the associate director for the Department of IT Technology Services serves as the main IT advisor to the director.
According to GAO, agency officials have acknowledged that the administrative office associate director does not have oversight of other office units, which instead manage their own IT workforces and projects.
“The judicial branch does not have a statutory requirement to establish a CIO. However, according to GAO’s prior work at federal agencies, leading organizations adopt and use an enterprise-wide approach to managing IT under the leadership of a CIO,” the watchdog added in its report.
GAO noted that the U.S. court system’s administrative office has implemented systems improvement recommendations for at least three of its largest IT projects: the judiciary electronic filing system, an enterprise facilities management system known as JSPACE, and its probation and pretrial services automated case tracking system.
Commenting on the report, Reps. Gerry Connolly, D-VA and Hank Johnson, D-GA, said: “This report does not paint a pretty picture of the status of information technology acquisition and management by the Administrative Office of the U.S. Courts (AOUSC). Simply put, it looks like the AOUSC doesn’t know how much its IT projects will cost, doesn’t have a handle on how IT’s money is spent, and doesn’t even know if its IT employees have the right skills and training.”
They added: “GAO documents that the AOUSC had no comprehensive cost estimates for the IT projects it evaluated, poorly constructed project schedules, routinely allowed serious cost overruns, and neglected its legal obligations to ensure that user fees are properly spent.”
The lawmakers said also that they expect AOUSC to work with them to establish in statute the position of CIO as recommended by the GAO.
Editor’s note: This story was updated to include comment from Reps. Connolly and Johnson.
Top commander expects drones strikes against US forces, partners in Africa
American forces in Africa and their partners will likely come under attack by armed drones operated by violent extremist groups in the not-too-distant future, the commander of U.S. Africa Command is warning.
Militant organizations in the Middle East have already employed such tactics using modified commercially available systems, Army Gen. Stephen Townsend noted during a meeting with the Defense Writers Group on Thursday.
“I don’t know why it is, but we haven’t seen that occur yet in Africa. But I suspect it’s coming any day,” he said. Small drones are “proliferating everywhere, rapidly. They’re low cost, and they can be quite effective and challenging to defend against.”
Townsend has first-hand experience coming under attack from unmanned aerial systems (UAS) while serving in Mosul, Iraq, in 2016.
“ISIS figured out how to arm their drones and attack us either with kamikaze explosive-laden drones or drones that dropped field expedient munitions or modified munitions. So they got pretty sophisticated with that,” he said.
Groups in Africa are already using UAS to support their operations, according to Townsend.
“We see them using drones for reconnaissance. We believe we’ve they’ve used drones for fire direction. The reason we believe that is we have had instances where drones immediately preceded mortar or rocket attacks or were there during the mortar or rocket attacks — so why else would you be doing that unless you’re trying to direct the fire?” he said. “And we’ve seen them precede ground assaults as well. I have not yet seen them come armed. But it won’t surprise me when it happens,” he said.
The Pentagon has been developing capabilities to counter these types of threats. Many of these efforts are being led by the Joint Counter-small Unmanned Aerial Systems Office (JCO).
African partners have already asked for U.S. assistance with counter-drone capabilities, according to Townsend.
“We are working on ways to help those partners that have that problem. For the most part, where the terrorists are sophisticated enough to have that capability is where our troops already are, for the most part. So that makes it a little easier. But that’s not true in all cases, and so we’re gonna have to look at how we help those partners. I think this is going to be a big problem for all of the Western partners to help with,” he said.
The U.S. military has been pursuing a variety of counter-UAS capabilities.
“We have a potpourri of these things, and some work better than others. This is not an easy thing to do to counter these things, because they change and evolve so rapidly. So if we had some kind of magic, you know, drone jammer that would get parked on our [forward operating base], or put in our vehicle that we could — when a drone shows up, we press a button and all the drones go away, that’d be awesome. I think that’s a growth industry,” Townsend said.
The Senate Armed Services Committee’s version of the fiscal 2023 National Defense Authorization Act would direct the Pentagon to come up with a new strategy to counter swarms of drones by state or non-state actors. The bill highlighted directed energy weapons — such as high-powered lasers or high-powered microwaves — as promising technologies that could help address the threat.
Townsend took the helm at Africom — which is headquartered in Stuttgart, Germany, and oversees U.S. military operations in Africa — in 2019. Last month, President Biden nominated Marine Lt. Gen. Michael Langley to be his successor and receive his fourth star. Langley is expected to be confirmed and become the Marine Corps’ first Black four-star.
Army set to field new cyber tool to improve situational awareness
The Army last month made a fielding decision for a critical cyber tool that will allow commanders to have a better understanding of their own cyber terrain.
The tool, Cyber Situational Understanding, is specifically designed for ground commanders to have better insight into the cyber and electromagnetic landscape to make more informed decisions. The tool is not meant to be used for cyberspace operations.
The Army in June approved fielding for the first increment of the program — which is focused on improving situational awareness of the friendly network and threats to it — with the first unit equipped in the August-September timeframe, according to program officials.
Division and corps are the priority echelons to receive this capability first with 11 such units slated to get the first increment from fourth quarter this year to third quarter next year, Lt. Col. Scott Shaffer, product lead for Mission Command Cyber at Program Executive Office Command, Control, Communications-Tactical, told FedScoop in a recent interview. That includes activity-duty and National Guard units.
As the Army is posturing to compete with more sophisticated adversaries, it is making the division the primary unit of action rather than the brigade combat team as seen during the global war on terror.
“For us, just as with the Army, the division is going to be our primary unit of action for Cyber SU,” Shaffer said. “Some of the information that Cyber SU receives is typically at a higher level anyways, so the challenge for us is collecting it at the right echelons and then sharing down at the lower levels as possible. Cyber SU could go to brigades as well. We’re just trying to find that right balance and what makes sense.”
Shaffer said the plan is still to develop and deliver on three increments or capability drops for the program. The team is currently working on wrapping development of the second capability drop, which will focus on seeing the battlespace. It will conclude development in the September-October timeframe and roll into a developmental test in November or December. After that, there will be an operational assessment with the 1st Armored Division.
The team has been working hand in hand with soldiers to get their perspective during the build process to ensure it meets their needs.
“A lot of the feedback we get is not necessarily how Cyber SU is tied into certain data sources, because I think we have a pretty good grasp, at least right now, for the initial capability in the friendly picture. We have a pretty good idea of the data sources that need to feed and be processed and analyzed in Cyber SU,” Shaffer said. “This is where user feedback really comes into play, is how do we want to present the data in a meaningful and a logical fashion where it’s actionable or soldiers and staff and commanders, if you will, can make a decision off of.”
Cyber SU is the first program specifically built for and with the Command Post Computing Environment (CPCE), a web-enabled system that will consolidate current mission systems and programs into a single user interface at the command post to provide a common operational picture.
While other systems will be folded into CPCE, to include the Advanced Field Artillery Tactical Data System (AFATADS), those platforms were previously standalone while Cyber SU is being built organically into it.
“We spent a lot of time developing the software. It was new. We spent a lot of time developing Cyber SU issue to function and operate inside the tactical common operating picture or single pane of glass, if you will, which is Command Post Computing Environment for us,” Shaffer said. “In my mind Cyber SU is paving the path for convergence for the Army. As far as I know, there’s probably other programs too, but it’s the first program to be fully converged with the Command Post Computing Environment … I think it’s nice to be a trendsetter or paving the path. I can appreciate some of the experiences I’m getting just down that path.”
CPCE recently completed Milestone B for its Increment 2 in June as well, which is the beginning of the engineering and manufacturing development phase.
This increment will field as part of the Army’s Capability Set 23. These capability sets are incremental builds in two-year timelines for the Army’s integrated tactical network. Capability Set 21 was primarily designed for infantry brigades, Capability Set 23 is focused on Stryker brigades, and Capability Set 25 is focused on armored brigades.
Officials explained to FedScoop in a trip to Aberdeen Proving Ground in June that Increment 2 includes a tactical data fabric, logistics requirements and converging applications.
The CPCE team has been working with I Corps at Joint Base Lewis-McChord in some of their exercises to gear up for Project Convergence 22, when the Army will experiment with a variety of technology.
In regards to the tactical data fabric, officials explained they are working to integrate existing Army technologies. This includes working with Army Cyber Command on a tactical instantiation of its big data platform called Gabriel Nimbus.
Several so-called big data platforms exist across U.S. Cyber Command, the Defense Information Systems Agency, Army Cyber Command and the Marine Corps. They are essentially hybrid cloud environments that allow for storage, computation and analytics across networked sensors. When forces conduct cyber missions, they collect data and use high-powered analytics to make sense of it. Big data platforms do just that, but also share that analysis in an easy-to-access repository for other forces.
The idea here is to convert the Army’s system to one more tactically focused for ground forces, rather than stationary cyber forces conducting missions from faraway locations.
There is an agreement between ARCYBER and Program Executive Office Enterprise Information Systems to provide that capability to Army Pacific to familiarize itself with it and eventually take it to Project Convergence.
The goal is to pull data from various sources to get a persistent data layer and present a better picture so the right feeds of information go to the right people in a timely manner to make faster decisions.
The other effort involves merging something called Project Rainmaker, which was an Army science and technology effort that explored the concept of data fabric. Officials have previously said it has been helpful in allowing the Army to understand the blueprint so it can start to translate that into the procurement phase and find the balance between commercial solutions and government technology.
Rep. Rosendale: Oracle Cerner EHR rollout is a ‘little game of disaster’
The rollout of the Department of Veterans Affairs’ new electronic health records system has been a “total mess” from which IT vendor Oracle Cerner has been able to profit, according to a senior Republican.
Rep. Matt Rosendale, R-MT., said that VA Secretary Denis McDonough should take responsibility for major flaws and ongoing risks to veterans associated with the platform.
“It’s a s*** show. They’ve made a total mess out of it,” the lawmaker told FedScoop. “Meanwhile Cerner is profiting off this debacle. They’re profiting from it. This is unacceptable. It’s a little game of disaster.”
Rosendale, who is the House VA Subcommittee on Technology Modernization Ranking Member, added that it was incumbent on McDonough to hold everyone involved in the EHR program accountable.
“At the end of the day Secretary McDonough has to take responsibility for it because he’s in charge of the VA. So it’s up to him to hold everyone else accountable,” he told this publication outside a House hearing Wednesday on the issue.
The senior Republican’s trenchant criticism came after lawmakers from both parties aggressively called out rampant issues with the cost, transparency and reliability of the VA’s electronic health record (EHR) system rollout during the House hearing. They were speaking at a House committee on Veterans’ Affairs hearing Wednesday on patient safety and the electronic health record modernization program.
Multiple Congressmen speaking at the hearing were angry that despite internal VA reports from October 2021 showing that the EHR system had major flaws and ongoing risks that could harm veterans, Secretary Denis McDonough and the VA continued to launch the system in medical facilities in multiple states.
Rosendale also accused the VA’s Executive Director of the EHR Modernization Integration Office at the VA Terry Adirim, and her staff, of contradicting themselves during their interactions with him and during hearings in Congress.
The implementation of the VA’s new EHR system on an Oracle Cerner developed platform to medical centers around the country will be delayed from its original estimates by at least one to two years and the system rollout is far behind where it was expected to be at the moment, a top VA executive said during a Senate hearing last week.
The EHR system rollout issues have in some instances, including at the center in Spokane, Washington, caused major harm in which a veteran at risk for suicide did not receive treatment because records disappeared in the computer system. This system error occurred due to technical issues with what’s known as an “unknown queue,” that has caused nearly 150 instances of patient harm, according to the VA’s Office of Inspector General (OIG).
The Institute for Defense Analyses, a nonprofit research entity, puts the life cycle cost of the EHR system at $50.8 billion over 28 years, while the VA’s original rollout implementation tag was about $10 billion over 10 years, but some Congressmen are even skeptical of these estimates.
“The new [IDA] estimate says the cost could be as high as $63 billion if everything goes wrong, and I see a lot of things going wrong,” said Rep. Mike Bost, R-IL, a member of the House VA Subcommittee on Technology Modernization.
“Cerner says the rollout would be 13 years instead of 10, but even 13 years seems like a best case scenario given all the issues,” said Bost.
Oracle-Cerner said during the House hearing Wednesday that problems with the VA’s current cost estimates are due to the federal government assuming the EHR technology stands still. However, the company took responsibility for the VA EHR software being too complicated and cumbersome, requiring extensive staff training which typically shouldn’t be the case.
Adirim from the VA during the House hearing Wednesday attributed some of the increased EHR rollout costs to Oracle-Cerner contract modifications regarding pharmacy enhancements that went above and beyond the baseline of the original contract because they were “technically considered enhancements,” not fixes to the system, Adirim said.
Rep. Rosendale, however, said that Oracle Cerner was getting paid more money for their contract while veterans continued to get poor service at medical facilities where the EHR system has been rolled out without permanently solving latent issues with reliability and stability.
Former VA leaders who have experience with EHR systems have also observed deep entrenched issues with the agencies ongoing rollout and its ballooning costs.
“If you don’t have discipline, if you don’t control costs tightly and if you don’t even know what your costs are, you’ll get sucked for every dollar the government has. Like with Cerner. That’s how this game works,” said Roger Baker, chief information officer (CIO) and assistant secretary for information and technology for the Veterans Affairs Department from 2009 to 2013.
“The VA doesn’t know how much things cost and it has no clue how to do so, it would be like me trying to estimate what it could cost to build the Empire State Building,” he said.
Baker added that the VA had repeatedly shown management and execution issues with the EHR rollout due to their lack of prioritization on the day-to-day experience of doctors and staff within VA hospitals while instead focusing on trying to expand the rollout to as many medical facilities as quickly as possible.
Adirim declined to comment further after the hearing.
Saltzman tapped to lead Space Force
President Biden has nominated Lt. Gen. B. Chance Saltzman to be the next chief of space operations, the Pentagon announced Thursday.
If confirmed by the Senate, he would become a member of the Joint Chiefs of Staff and the Space Force’s top officer as the service tackles major challenges such as defending U.S. space assets against threats posed by advanced adversaries; acquiring new communications, intelligence, surveillance and reconnaissance capabilities; and pursuing the Pentagon’s Joint All-Domain Command and Control (JADC2) concept.
Saltzman is currently serving as the deputy chief of space operations for operations, cyber and nuclear. where he oversees operations, intelligence, sustainment, cyber, and nuclear issues for the Space Force.
If confirmed by the Senate, he would become just the second-ever chief of space operations, succeeding Gen. John “Jay” Raymond, who became the first person to hold the position after the Space Force was established as a separate branch of the military in 2019.
Saltzman has a long history of serving in space-related positions at the Defense Department during his career, including Chief , Combat Plans Division, Joint Space Operations Center; Chief, Combat Operations Division, Joint Space Operations Center; Commander, 614th Space Operations Squadron; Commander, 1st Space Control Squadron; Commander, 460th Operations Group; Commander, Aerospace Data Facility; Deputy Director, Plans and Programs, Headquarters Air Force Space Command; Executive Officer to the Commander, Air Force Space Command; and satellite operator for the National Reconnaissance Office, according to his DOD bio.
His confirmation hearing has not yet been scheduled.
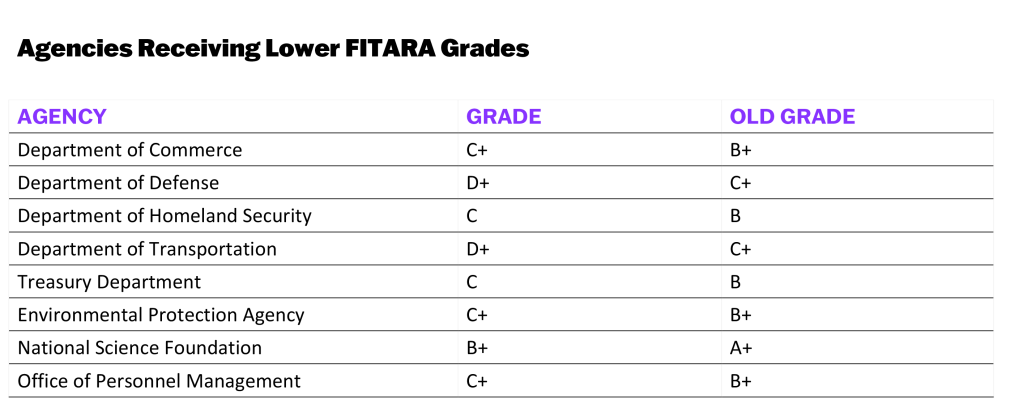
8 agencies receive lower FITARA grades following scoring changes
The FITARA grades of eight agencies have fallen after the House Oversight Committee revised the methodology used to assess federal government departments’ IT modernization progress.
Agencies whose scorecard grades decreased were the departments of Commerce, Defense, Homeland Security, Transportation, and the Treasury; Environmental Protection Agency; National Science Foundation; and Office of Personnel Management.
The Nuclear Regulatory Commission was the only agency whose grade increased from a C- to a B.
FITARA scorecard grades were first issued in November 2015 as a means of monitoring agencies’ progress in implementing cybersecurity and IT modernization improvements required under the Federal Information Technology Acquisition Reform Act (FITARA). They are issued twice a year by the Government Accountability Office.
Recent changes to the assessment methodology included the retiring the Data Center Optimization Initiative (DCOI) component.
FITARA requires agency chief information officers (CIOs) to certify IT investments are achieving incremental development, and committee staff reverted to letting CIOs self-certify software development projects for the 14.0 scorecard. The 24 Chief Financial Officers Act agencies reported one more acting CIO than in January, bringing the total to three.
Lawmakers made changes to the grading methodology after all agencies received As on the FITARA 13.0 scorecard in January and the cybersecurity component was adjusted due to a lack of cross-agency priority (CAP) goal data.
Agencies’ FITARA grades stagnated in the last two scorecards, which Rep. Gerry Connolly, D-Va., attributed to a failure to incentivize them to improve their IT — given the limited data available and tight six-month turnaround for grading. Connolly chairs the Government Operations subcommittee that holds hearings on the scorecard like the one Thursday morning.
Despite the changes in methodology for FITARA 14.0, 15 agencies’ grades remained the same. That number would have been 20 under the old methodology, and four agencies would have increased their grades.
Committee staff replaced the scorecard’s DCOI component with a new data center consolidation component addressing future planned closures, which is previewed but not included in agencies’ overall grades yet. Seven agencies have no plans for future data center closures.
Agencies continue to struggle with the transition from the General Services Administration’s expiring telecommunications contracts to the $50 billion Enterprise Infrastructure Solutions (EIS) contract for network and infrastructure modernization. They were expected to be 90% transitioned by March and 100% transitioned by September.
Eleven agencies received Fs for their EIS transitions, four fewer than last time. GSA, itself, raised its F grade to a D since January.
Senate committee waves through Prabhakar OSTP director nomination
The Senate Commerce Committee approved Arati Prabhakar to be director of the White House Office of Science and Technology Policy, the first woman of color and immigrant to hold the position, Wednesday.
Senators urged Prabhakar, who previously served as director of the Defense Advanced Research Projects Agency and the National Institute of Standards and Technology, to coordinate agencies’ competing emerging technology priorities during her nomination hearing July 20.
Her proposed appointment will now proceed to the Senate floor for a simple majority vote.
President Biden nominated Prabhakar for the post on June 21 to replace Acting Director Alondra Nelson, who filled the vacancy left by Eric Lander when he resigned over disrespecting and demeaning staff and women, in particular, according to multiple staffers’ accounts.
“While I am happy to see another accomplished woman at the forefront of the federal government’s scientific community, I am just as heartened by her commitment to put people at OSTP first, and I am pleased to support her nomination,” said committee chair Sen. Maria Cantwell, D-Wash., ahead of the vote. “If confirmed, she will be tasked with elevating OSTP’s role to ensure the U.S. remain a global leader in STEM, increasing investments in R&D, promoting greater diversity in the sciences, improving our weather forecasting capabilities, and protecting our scientific research.”
Prabhakar expressed hope the U.S. Innovation and Competition Act (USICA) would be made law — allowing her to establish a working group coordinating activities in key technology areas like artificial intelligence and quantum computing — at her nomination hearing.
She also said fundamental research should be conducted openly for the benefit of the research community, while product development and applied work protected from foreign competitors like China.
USICA would also require agencies to submit comprehensive science and technology strategies.
“One thing I want to do is respect and honor those different missions, and then I want to knock down barriers to help those different parts of our federal R&D enterprise achieve those missions,” Prabhakar said at her nomination hearing. “And I want to knit them together, so that they can do the things together that they can’t do separately.”
China allegedly tapped computers and phones of Fed employee, Sen. Portman says in report
Chinese officials allegedly compromised IT equipment belonging to a Federal Reserve employee and copied information from the individual’s WeChat account, according to a report published yesterday by the Senate Homeland Security and Governmental Affairs Committee.
An investigation by minority staff on the committee alleges that the equipment was compromised while the Fed employee was detained four times by Chinese government staff during a trip to Shanghai in 2019.
Officials working for China also used threats against the individual’s family in an attempt to coerce him to provide economic information and assistance, according to the report. Information copied from the detained Fed employee’s WeChat account included contact details for other federal government employees.
The report stated that China has targeted the U.S. Federal Reserve System since at least 2013, with the intention of undermining American economic and monetary policy. A 2019 bipartisan report previously detailed how China uses talent recruitment programs, including the Thousand Talents Plan, to target science and technology sectors.
The espionage allegations emerge amid heightened tensions between the U.S. and China, and after the Chinese government earlier this week warned of “serious consequences” if a trip to Taiwan by House Speaker Nancy Pelosi, D-Calif., goes ahead as planned.
The report also comes as widespread concerns over the ability of the Chinese government to compromise U.S. government IT systems. These include the prospect that China may be leveraging American-designed semiconductors to enhance its artificial intelligence capabilities, which may have sweeping civilian and military applications.
In the realm of quantum technology, where China and other nation states have made significant recent advances, cybersecurity leaders have warned that the technology may be used to break the public-key cryptography that secures most federal systems.
Sen. Rob Portman, R-Ohio, who led the report, said: “This investigation makes clear that China’s malign efforts at influence and information theft are not limited to science and technology fields — American economic and monetary policy is also being targeted by the Chinese government.”
“I am concerned by the threat to the Fed and hope our investigation, which is based on the Fed’s own documents and corresponds with assessments and recommendations made by the FBI, wakes the Fed up to the broad threat from China to our monetary policy,” Portman added. “The risk is clear, I urge the Fed to do more, working with the FBI, to counter this threat from one of our foremost foreign adversaries.”
China’s embassy in Washington D.C. did not respond to a request for comment.
Contract award imminent for EITaaS Wave 1, Air Force CIO says
The Air Force is “close” to issuing a contract award for Wave 1 of its Enterprise IT as a Service (EITaaS) initiative, according to the chief information officer.
A few years ago, the Air Force embarked on outsourcing much of its IT functions to private industry to free up its own personnel from doing mundane network activities so they could focus more on proactive functions such as hunting threats on the network. Wave 1 of EITaaS serves as an upgrade with improved and consolidated service desks as well as a catalog for more than 700,000 users worldwide, according to the Air Force. Wave 1 is also the first effort to expand from the initial EITaaS risk reduction effort.
Speaking at a forum hosted by the Potomac Officers Club on Tuesday, Air Force CIO Lauren Knausenberger said she expects Wave 1 to be awarded “any second now,” adding “I can’t tell you a date yet, but I know we’re close.”
Knausenberger noted that Wave 1 is fully funded.
With Wave 1, for the first time, she said, the Air Force will have enterprise IT service management, one platform and one easy way to enter a trouble ticket. Ideally, it will allow for the use of analytics and other tools to identify issues in the enterprise and go after those, as opposed to waiting for the trouble tickets to come in.
There will also be a wider variety of end user devices as well as an easier way to order them.
As for Wave 2, Knausenberger said the scope is still changing as the Air Force moves toward industry days and draft requests for proposals. At the very least, it will include overhauling base infrastructure. Around 30 bases are prioritized for Wave 2, she said.
“I suspect that the money will come when one of our industry partners knocks it out of the park and shows us that that next generation architecture makes a huge impact for unclassified and secret warfighting capabilities as well as a huge impact to our business capability, our ability to fight with our allies and our ability just to be more efficient in our day-to-day business,” she said.