Senate looking for DevOps support
The U.S. Senate is looking for a potential DevOps contractor to provide outsourced engineering and operations support.
The Office of the Sergeant at Arms posted a sources sought notice to FedBizOpps on Monday in an attempt to build a “bidders list” for this requirement. The ideal respondent would be able to provide engineering services for the Senate’s Red Hat OpenShift application platform, maintain and update the environment and provide support services.
Based on responses to the market survey, the Senate Sergeant at Arms intends to invite qualified contractors to submit proposals. If the notice yields “suitable responses,” it will post a solicitation in the fourth quarter of fiscal 2019.
DevOps, the process of integrating an organization’s engineering (Dev) and operations (Ops) teams in order to approach engineering processes in an agile and iterative manner, is a popular buzzword both inside government and out. It’s generally considered a best practice for federal IT modernization. But what it actually means is a matter of some contention — even people in charge of working with this popular practice tend to provide definitions that highlight differing aspects of it.
Responses to the Senate’s notice are due by May 28.
CIA launches official Tor site to communicate on dark web
The CIA has recently been expanding its online communication with the public, and now it’s taking that effort to the deepest corners of the internet.
The agency launched a website Tuesday on the Tor network — the backbone of what’s commonly known as the dark web — to give people a new and more secure way to get in contact.
“Our global mission demands that individuals can access us securely from anywhere. Creating an onion site is just one of many ways we’re going where people are,” Brittany Bramell, CIA’s director of public affairs, said in a statement. The dark web isn’t indexed or searchable by normal search engines, and to access it, individuals must use an anonymized browser called Tor — short for The Onion Router.
The CIA’s .onion site will provide all of the same information, contacts and services the spy agency’s normal website does. It’s aimed at people who want to anonymously share information with the CIA, but are wary of being tracked.
“We believe onion services are a key next step in securing the web, similar to the standardization of https as more secure configuration than http, so it’s not a surprise that the CIA would want to take advantage of the privacy and security protections that onion services provide,” said Stephanie Whited, Tor’s communications director.
Spy agencies have long been at home on the dark web, as Tor was developed with U.S. intelligence in mind by the Naval Research Lab “for the primary purpose of protecting government communications.” But now it’s used by a much wider community, from journalists and activists to those buying and selling illicit goods and services.
The CIA gives instructions on downloading Tor and how to reach its dark web domain, which is at the following address:
ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion
This comes on the heels of the CIA launching an official Instagram account, adding to a social media presence that already consisted of Twitter and Facebook profiles.
White House celebrates ‘outstanding’ employees with Gears of Government awards
The White House recognized 24 federal employees at seven agencies Monday with the President’s Gears of Government Award.
Developed in 2018 by the Office of Management and Budget, the awards recognize federal employees “whose performance and dedication support exceptional delivery of key outcomes for the American people: mission results, customer service, and accountable stewardship,” according to the guidance memo.
The winners are:
-
Department of Veterans Affairs (VA): Barbara C. Morton
-
Department of Health and Human Services (HHS): Dr. Kathleen Uhl, Kenneth Kraft, Dustin Litwiler, Jess Weisz, Cassandra Newsome, Roman Kulbashny, and Dr. Emily Haas
-
National Oceanic and Atmospheric Administration (NOAA): Gregory Doucette, Timothy Davis, and Stephanie Moore
-
Department of Transportation (DOT): Kerry Kolodziej, Kara Fischer, Stephen Hench, Luicia Sanchez, and Nicholas LaBruna
-
U.S. Department of Agriculture (USDA): Roger Cryan, Marc McFetridge, Michael Sheats, and Robert Wintersteen
-
Department of Energy and NASA KRUSTY Team: Marc Gibson, Lee Mason, William Pulse, and Angela Chambers
Given out during Public Service Recognition Week, the awards are “a perfect opportunity to recognize outstanding federal employees … in order to highlight the fact that every day, federal employees play a key role in our lives,” Margaret Weichert, deputy director of management at OMB, said during a press call. “Whether they’re defending the homeland, inspecting our food, making scientific discoveries or managing our cyber borders, this work requires faithful dedication to the mission of our federal government, and that’s what each recipient demonstrates.”
As set forth in the 2018 memo, agencies were given the opportunity to recognize employees with their own Gears of Government awards and nominate them to OMB and the White House for the President’s awards.
Weichert highlighted that, in addition to the focus on “mission, service and stewardship,” the administration placed an emphasis on recognizing employees outside the Beltway and those who play support roles within their agencies.
“We wanted to explicitly call out not only the folks who have moved forward the mission of each of their agencies but also those who have showcased how we in support capabilities can also improve the lives of Americans by improving customer service and also being dedicated to stewardship of taxpayer resources,” she said.
Weichert continued, “Very often you’ll see emphasis paid to some of the groundbreaking work we do in science, technology, engineering and math, medicine … places like NASA and elsewhere tend to have a lot of very high profile projects. But we also wanted to say when we really look at where our feds are making a difference, in a lot of cases, it’s not as well known and we wanted to give an opportunity for those to shine.”
Awardees will be recognized during a ceremony at the White House later this month.
TSA pipeline cybersecurity under review
The Government Accountability Office is currently reviewing the process for updating pipeline security guidelines to better protect the cybersecurity of the critical infrastructure, according to a recent report.
The Transportation Security Administration oversees the physical security and cybersecurity of more than 2.7 million miles of computerized, interstate pipeline systems used to transport oil, natural gas and other hazardous products. These systems “are attractive targets for hackers and terrorists,” according to the GAO report.
In December, GAO found TSA lacked a process to determine when to update voluntary security guidelines for pipeline operators — among nine other weaknesses — prompting the latter to submit new procedures in April.
“A minor pipeline system disruption could result in commodity price increases, while prolonged pipeline disruptions could lead to widespread energy shortages,” said William Russell, acting director of GAO, in his written testimony to the House Energy Subcommittee. “A disruption of any magnitude may affect other domestic critical infrastructure and industries that are dependent on pipeline system commodities.”
The FBI reported a nation-state targeted organizations across multiple critical infrastructure sectors, including the energy sector, in March 2018 seeking information on industrial control systems.
TSA security reviews of pipeline systems have “varied considerably over time,” according to the report, which the agency attributes to a workforce shortage. A strategic workforce plan specifying the required level of cybersecurity expertise members of TSA’s pipeline security branch are expected to have is anticipated in July.
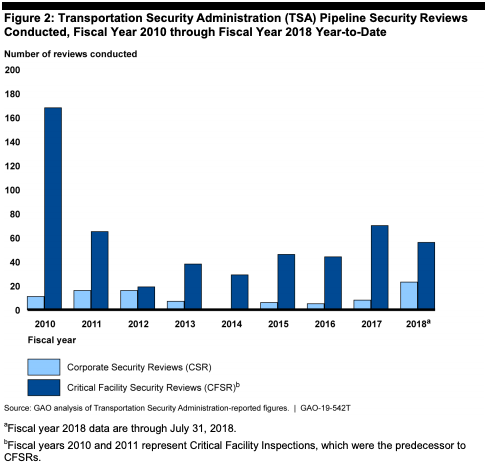
GAO also found TSA hasn’t updated its risk assessment methodology since 2014, and the data sources tied to its risk ranking tool aren’t fully documented or up to date. TSA in April reported taking steps to address those problems.
Corporate security reviews and critical facility security reviews of the 100 most critical pipeline systems remain at the owner’s discretion. By November, TSA plans to begin tracking security review recommendations from the past five years.
White House seeks new contractor for IT support services
The White House Office of Management and Budget is in the early stages of looking for a new contractor to provide supplemental IT support services.
OMB posted a request for information to FedBizOpps last week — responses by interested entities are due May 9.
The selected contractor would be responsible for “supplemental OMB specific work” outside of what the White House’s Office of the Chief Information Officer already takes care of. For example, the contractor would tend to OMB’s private cloud, and work on “special projects” as the need arises. The contractor would also act as a supplemental service desk provider for OMB employees — a performance work statement specifies that there were over 1,500 trouble tickets (on everything from hardware to access management) submitted in 2018.
The estimated period of the contract is July 31, 2019 through July 30, 2020, with four available and optional one year extensions. OMB also plans to have the new contractor work side-by-side with the current provider for a month or two at the beginning of the contract to complete the necessary “knowledge transfer.”
Interested companies are asked to describe their capabilities and a time that they have completed similar work for another government agency in the past.
How modernized networks can accelerate DOD’s multicloud migration plans
The Department of Defense’s transition to an enterprise-level multicloud environment is enormous, both in scale and complexity.
And so are the potential benefits of deploying modern, tried-and-tested network solutions that can integrate the DOD’s disparate public, private and hybrid clouds into an agile, secure and ubiquitous infrastructure, suggests a new briefing report.

Read the full report.
The report, “Why open standards-based, modular networks are key to DOD multicloud migration,” highlights how a software-defined networking (SDN) platform, operating at the network overlay and underlay levels, represents an essential building block in achieving DOD’s cloud migration strategy.
The networking approach would benefit DOD operations in a number of ways, according to the report, by:
- Accelerating the ability to integrate “general purpose” and “fit-for-purpose” clouds.
- Reducing the need to locate network specialists around the world by centralizing network management.
- Increasing network performance and reduce application downtime.
- Capitalizing on continuous technology advances and best-of-breed providers while avoiding vendor lock-in.
- Reducing network operating and support costs.
The report, written by FedScoop and sponsored by Juniper Networks, notes that IT teams across the DOD are working to deploy cloud platforms and migrate or develop applications that support their mission initiatives. However, it highlights ways DOD’s cloud migration strategy can be significantly enhanced by developing a “multicloud, multivendor networking environment with a unified cybersecurity architecture and simplified operational command and control.”
The DOD acknowledges it faces a number of challenges migrating to the cloud, including inadequate efficiency and security in IT, disjointed cloud implementations and disparate cloud architectures. That’s hampered DOD’s ability to provide common data and infrastructures to enable AI, as well as a number of other strategic objectives, according to the DOD’s cloud strategy, released publicly in February. The Pentagon is trying to address a portion of those challenges through its Joint Enterprise Defense Infrastructure (JEDI) and its Defense Enterprise Office Solutions acquisition contracts currently up for grabs.
In the cloud strategy document, Acting Secretary of Defense Patrick M. Shanahan said, “The Department of Defense has entered the modern age of warfighting where the battlefield exists as much in the digital world as it does in the physical. Cloud is a fundamental component of the global infrastructure that will empower the warfighter with data and is critical to maintaining our military’s technological advantage.”
The briefing report offers a number of considerations and resources for designing enterprise-scale networking platforms. And it points to the kinds of overall IT improvements that can be achieved by adopting open standards based, modular networks.
The report cites an IDC research study that assessed the impact of deploying enterprise-scale networking solutions from Juniper Networks, including Contrail Enterprise Multicloud, at large-scale enterprises across the world. Those organizations collectively reported:
- 56 percent lower cost of operations
- 41 percent improvement in application performance
- 98 percent less unplanned downtime
- 44 percent more efficient network infrastructure staff
- 3 times more staff time for innovation
“[Defense agencies] don’t really know what the future will hold as far as what percentage of their workload is going to be in the cloud and where the applications they are purchasing are going to be developed – and what platforms they need to manage to be able to support them,” says Ian Peterson, a senior engineer at Juniper Networks. “Another uncertainty is what security mandates are going to come down the pike.”
The best way forward given the unknowns, says Peterson, is to move toward a single software-defined networking (SDN) platform model, capable of spanning physical, virtual and cloud infrastructures, he said.
“Leveraging open standards allows you to take advantage of the best of the best without being locked into a vendor,” added Mike Loefflad, systems engineering manager at Juniper Networks. It also supports a wider range of APIs for more seamless integrations.
By giving DOD units the ability to have a more agile, scalable and ubiquitous network model, its IT operations can scale and deploy applications faster and better accommodate the growing use of mobile and Internet of Things devices.
If the DOD can overcome challenges to its cloud strategy, the benefits of implementing open SDN networks would be worth its efforts.
Read the full report to learn about SDN capabilities and benefits.
This article was produced by FedScoop and sponsored by Juniper Networks.
DOD’s reskilling overhaul starts with an OPM platform
The Department of Defense entered into an agreement Friday to use the Office of Personnel Management’s workforce training platform to streamline its own reskilling efforts.
USALearning began as an e-government initiative in 2004 and already supports more than 100 small agencies governmentwide with cloud-based learning systems.
Over 18 months, DoD’s IT and Business Systems Reform Team identified more than 50,000 disparately managed learning courses across 161 distinct learning management systems it hopes to rein in by creating an online common course catalog and common learning record repository.
“Moving to the USALearning platform will reduce the redundancy in common learning courses and allow us to move to a DOD-wide common course catalogue,” Lisa Hershman, acting chief management officer at DOD, told reporters at the signing of the memorandum of agreement. “This is a pivotal step in becoming easier to do business with.”
The department estimates it will save $22 million in 2020 and $122 million over five years through cost-optimized training and education products and services. Hershman said she’d like to see the approximately 1,800 Pentagonwide business systems reduced to 25 in time.
DOD oversees the largest population in government, spending 304 million hours on learning annually. About 40,000 federal civilians change positions within DOD a year, a process that inevitably leads to unnecessary retraining that can run eight to 10 hours, said Margaret Weichert, acting director of OPM.
“If you change jobs and you did — let’s say a cyber training in one job — it doesn’t mean that you’re going to get credit for that at your next job if it’s on a different system,” Weichert said. “You could actually be paying to train the same person twice in one year for a routine activity.”
Kelly Sims will serve as program manager of category management for training and education, the functional lead of DOD’s transition to USALearning. Her team is still being formed, but work is already being done to distill trainings down into competencies.
“Relative to the common course catalog, one of the challenges in DOD — and actually across government — is we all call courses different things, and a lot of those courses aren’t specifically designed at the competency level,” said William Peratino, deputy director of new and emerging human resources technologies at OPM.
“If you take that competency-based model, overlay it across the workforce, you can then distribute the workforce where you need them, when you need them, in specific roles and locations,” he added.
USALearning is developing a career readiness portal for DOD so employees can get information on the courses they need to take to reach the next level of proficiency by searching for the relevant competencies.
DOD employees will have one learning record, and outcome data will be among the platform metrics looked at to determine what annual trainings are necessary.
“It’s premature to say what’s the right number of courses because there’s a lot of redundancy that we need to identify,” Weichert said.
DOD may find other competencies in areas like cybersecurity aren’t being taught, leading to the creation of new courses, she added.
The department already has an advanced distributed learning initiative for testing emerging learning technologies, and USALearning will be able to deploy those across agency partners — a list that is expected to grow.
Weichert said there are “clear intersections” between what DOD is doing and the recently announced Federal Cyber Reskilling Academy, so OPM is seeking “highly interoperable, interconnected platforms.”
USALearning’s platform is “essentially a white-label solution,” she added.
Pentagon sends software acquisition study to Congress
The Department of Defense announced Friday that it has officially sent the Software Acquisition and Practices (SWAP) study prepared by the advisory Defense Innovation Board to Congress.
“The report, I think, is an energizing product,” Ellen Lord, undersecretary of defense for acquisition and sustainment, said during a press conference. It “coincides with renewed and palpable momentum to quickly evolve our approach to software acquisition and development.”
Lord said that work on some of the 10 primary recommendations made in the report is already underway. The report’s “draft implementation plans,” are especially helpful, she added. Her team is working to finalize its implementation course of action and plans to deliver an overview to the defense oversight committees within 60 days.
With the delivery of the congressionally mandated document, though, the Pentagon is asking the legislative branch to play its part in modernizing defense software acquisitions. “The department has the authorities it needs to modernize its approach to software development,” Lord said. But she also called elements of the current acquisition process “too onerous.”
“The department calls upon Congress to provide explicit and specific authorities for software, such as a new appropriations category to fund software as a single budget category,” she said.
The SWAP study, which was mandated by the fiscal 2018 National Defense Authorization Act, is the culmination of the Defense Innovation Board’s efforts to understand how the defense agency acquires software and how it could do better. It all boils down to 10 recommendations structured around three themes and four areas of effort.
The three main themes in the report are:
- Speed and cycle time are the most important metrics for software;
- Software is made by people and for people, so digital talent matters; and
- Software is different than hardware, and not all software is the same.
The four “lines of effort” the board recommends to realize these three themes are:
- Refactor statutes, regulations, and processes for software;
- Create and maintain cross-program/cross-service digital infrastructure;
- Create new paths for digital talent (especially internal talent); and
- Change the practice of how software is procured and developed.
DIB members and study leads Richard Murray and Michael McQuade both acknowledged Friday that studies showing the challenges to acquiring software at DOD have been done before. However, both expressed optimism that this study, with its specific recommendations and ways to move forward, will be successful.
“We think this is the right time,” Murray said. “We just need to start moving forward and actually go do something.”
Patent and Trademark Office looks to stabilize critical IT apps
The U.S. Patent and Trademark Office issued a request for information Wednesday for an initiative to stabilize critical IT applications.
Patent and trademark applications have more than doubled since 2000 to upward of a million filed in 2017 — most electronically. The office is attempting to “support the shifting technology needs” of its approximately 8,000 examiners and 5,000 support staff, but its Office of the CIO needs to upgrade aging technology across the organization, according to the RFI.
In a recent assessment of its 300-plus IT application portfolios, USPTO identified those most at risk, including its patent search, electronic filing, and patent enterprise text search systems among others.
“As the USPTO explores the strategic direction it will take to best incorporate new technologies into patent and trademark proceedings, the agency is assessing the value of a concentrated effort that will bring a set of identified applications into a consistent infrastructure level,” reads the RFI. “The intent is to enable longevity and minimize disruptions by bringing the identified applications into a consistent state that the agency will be able to support in an efficient and effective manner.”
A vendor is needed to provide technical project management and onsite engineering support, as well as establish performance metrics.
The RFI closes May 13.
White House targets federal cybersecurity workforce development in new executive order
This story first appeared on CyberScoop
The White House is rolling out an executive order that is intended to bolster the nation’s cybersecurity workforce, senior administration officials told reporters on a call Thursday.
The officials detailed a document that includes provisions geared toward the federal government’s employees, as well as education and career development initiatives for the U.S. workforce in general. The goal is to build a “superior cybersecurity workforce,” one official said.
The White House wants to create a President’s Cybersecurity Cup competition that “will identify, challenge, and reward the government’s best personnel supporting cybersecurity and cyber excellence,” the officials said. Other elements include allowing cybersecurity employees to rotate among agencies, and using new cybersecurity aptitude tests as part of efforts to reskill federal workers.
The employee-rotation idea already has bipartisan support on Capitol Hill, with Senate passage earlier this week of a bill that would put it into action. The Trump administration has embraced reskilling for awhile, too: A program to train existing federal employees to fill cybersecurity jobs is looking to fill its second cohort.
The order also aims to reward teachers across the nation by establishing a “Presidential Cybersecurity Education Award” for elementary and secondary school educators who demonstrate “superior accomplishments,” one official said.
There are currently approximately 320,000 open cybersecurity jobs in the U.S., according to CompTIA. This comes at a time when the Federal Bureau of Investigation is reportedly bleeding talent just as Director of National Intelligence Dan Coats and other officials have noted that cyberthreats from foreign nations are increasing. The U.S. departments of Commerce and Homeland Security assessed last year that the U.S. “needs immediate and sustained improvements in its cybersecurity workforce situation.”
The details of the President’s Cybersecurity Cup Challenge and how it will work are still in gestation phases, the officials said. The government will examine how other challenges on the collegiate and national scale, for instance, organize similar cybersecurity competitions, one official said.
The order will establish “cybersecurity aptitude assessments” that federal agencies may use to identify and reskill current employees with “cybersecurity potential” and “basic raw skills,” as one official put it. The test will be developed with the National Institute of Standards and Technology and the Office of Management and Budget, one official said.
President Trump’s creation of a federal rotational cybersecurity program is “consistent” with the Senate-passed legislation, one official said. This goal of the program is to “ensure that we have consistency in training and standardization in the federal workforce across the federal government,” one official said.
The executive order links all of its goals to the National Institute of Standards and Technology’s (NIST) National Initiative for Cybersecurity Education (NICE) framework, which delineates the differences between different kinds of cybersecurity jobs. The order encourages adoption of the NICE framework to help people identify what they need to do to get the cybersecurity job they want, senior administration officials said. The adoption of the framework is also intended to increase job mobility, per one senior administration official.