- Sponsored
- Modernization
The case for establishing an interoperable zero trust foundation for JADC2
Dan Schaaf is Senior Solutions Director and Army Sector CTO for GDIT, with more than 30 years’ experience implementing IT solutions and enterprise architecture for the U.S. Army and in the defense sector.
Defense officials for much of the past decade have recognized that future conflicts will require leaders to make decisions within minutes, or even seconds, and that the days of prolonged analysis are no longer an option. That concern was clearly spelled out more than three years ago by the National Defense Strategy Commission, which concluded that the state of the military’s Command and Control (C2) systems had “deteriorated” relative to potential competitors; and that the concept of a Joint All-Doman Command and Control (JADC2) network was clearly needed.
For all of the many strengths each of the services brings to the nation’s common defense, their central weakness remains the fact that the Air Force, Army, Marine Corps, Navy and Space Force each rely on separate and incompatible information networks. This reality leaves the Defense Department, and its ability to effectively defend and protect America’s interests, increasingly at risk.

Dan Schaaf, Senior Solutions Director and Army Sector CTO, GDIT
The vision for JADC2 is to create a single network to connect sensors to weapons systems and deliver information advantage at the speed of relevance. Currently the services are developing transformational IT capabilities tailored to their own needs, focused on cloud, data platforms and the implementation of zero trust. But for JADC2 to achieve warfighting capability, it is critical that DOD leaders put a stake in the ground and insist on establishing a set of common, foundational capabilities that will ensure that mission critical data can move across the DOD securely; data can be shared and analyzed where and when it’s needed; and the data can be trusted.
It is broadly accepted that a DOD-wide implementation of zero-trust security is foundational to the success of JADC2. But if DOD leaders do not establish critical zero trust capabilities, there are very real risks that as each of the services develop their own service-centric cloud environments and data platforms, they will also implement service-centric zero-trust capabilities. Ultimately this will increase the complexity of the operating environment and short circuit the DOD’s ability to access and exploit the relevant data and services required for joint and multi-domain operations.
To that end, DOD leaders should establish a foundational set of common zero trust capabilities and then require the services, the defense industry and our mission partners to use and ideally leverage those foundational zero trust capabilities.
The value of establishing a foundational DOD zero trust capability can be found in examining the use case of DOD’s decision to establish a PKI root certification authority for all identity and access management initiatives. By mandating the use of a common PKI root certification, the Defense Department created an environment that maintained and promoted cross-service interoperability and trust while still enabling each service to individually deploy identity and access management services.
Conversely, we can also learn from the DOD deployment of network directory services where they did not mandate the use of a trusted root. Though that deployment occurred more than two decades ago, the DOD still faces challenges to effectively federate and consolidate the multiple network domains that were created within the DOD, and which continue to significantly hamper efforts to develop a unified DOD network.
A way forward for cross-DOD zero trust
To further illustrate this point and conceptually describe what foundational zero trust capabilities should be developed, Figure 1 below is the GDIT zero trust architecture which demonstrates two key innovative concepts: 1) federated security enforcement and 2) centralized and data driven policy decision capability
Figure 1: GDIT Zero Trust Architecture
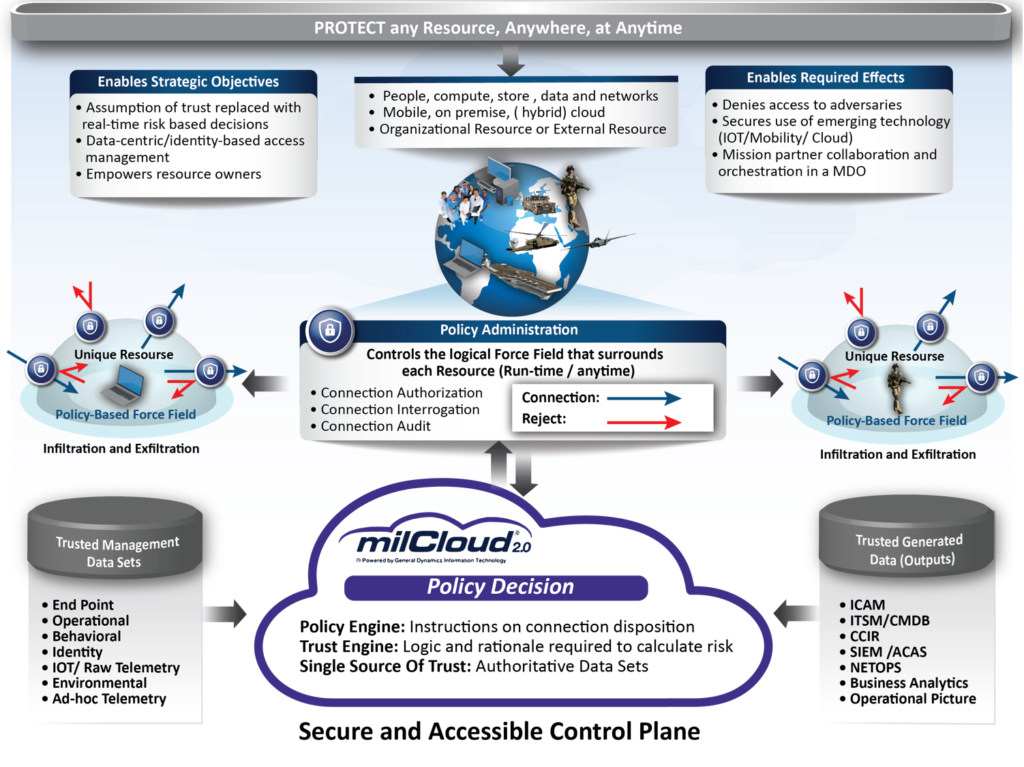
Source: GDIT
Along the center of Figure 1 is a “Policy Administration” capability that we propose. It represents the federated security enforcement devices which control the connection to resources. These are typically devices like firewalls or other access control mechanisms and are distributed throughout the enterprise today; but they also represent new and emerging zero-trust technologies that provide micro-segmentation of a network or dynamically establish software defined perimeters around resources.
Our recommendation for a foundational zero trust capability is the “Policy Decision” capability (along the bottom of Figure 1) which integrates a policy engine, a trust engine and a single source of truth. When centrally developed and managed, this capability will enable the DOD to incrementally deploy zero trust capabilities as well as integrate existing security enforcement devices.
To develop the “Policy Decision” capability, it’s critical that the DOD establishes the ground rules for what constitutes authoritative data — and ultimately lay the foundation for an enterprise-wide authoritative data environment. It’s also crucial that security enforcement systems working at machine speeds can discern what’s authoritative and what’s not in real time. That’s especially important as artificial intelligence within the trust engine is processing the data to determine relative risk and thresholds so that it is delivering the highest quality input to the policy engine that will synchronize the security enforcement devices and technologies.
Logically, the zero trust foundational capabilities should be delivered from a DOD cloud infrastructure to ensure the zero-trust management platform can operate securely and is also accessible by each service, the defense industry, mission partners and their data systems. Commercial clouds offer significant advantage for general purposes, but for joint operations, data must be integrated and served up without the friction arising from such factors as ingress and egress costs, data locality challenges or stovepipes resulting from disparate multi and hybrid cloud architectures among the military departments. Likewise, it makes sense for DoD’s own standardized capability for policy enforcement in support of JADC2 to be held in reserve, and not have different, even competing access regimes across the services.
A DOD Enterprise cloud is especially important for this use case. For those reasons, we are recommending DISA’s milCloud 2.0 cloud and contract as the location for the zero trust foundational capabilities. It can host the same innovative capabilities that leading edge companies host in the commercial cloud today; and it is located securely on DISA’s premises and inside DOD’s information networks. It is also FedRAMP-certified to meet DOD Impact Level 5 security ratings (and soon to be IL-6 certified) and it’s already accessible by all DOD components and authorized DOD partners.
By putting the foundational zero trust capabilities in place now and establishing a secure and accessible control plane for zero trust, DOD has a better chance of ensuring that they can protect any resource, anywhere and at any time. And just as importantly, it will accelerate warfighter capability by ensuring data from sensors, users and applications operating on and across JADC2 can be trusted and be used more universally.






