- Sponsored
- Sponsored Content
Closing the gaps in federal endpoint security

A new FedScoop study shows government agencies are making varying progress implementing methods to secure mobile smartphones, tablets, sensors, wearables and other endpoint devices accessing their networks.
However, the growing proliferation of devices accessing agency networks —including employees’ personal devices — is also increasing attack surface area for cyber threats. More than half of agency IT officials are concerned about network attacks from endpoint devices.
And while 6 in10 say securing government-issued mobile devices is a top concern over the next 12-18 months, many may be overlooking technologies they already have or own to address security concerns.
This online survey, conducted by CyberScoop and FedScoop and underwritten by Samsung, provides a new snapshot of what matters most to federal IT and security leaders in securing endpoint devices accessing their networks — and where key gaps remain. The study surveyed qualified federal government information technology and cybersecurity officials who have decision making responsibility or influence regarding cybersecurity services, solutions, requirements, budgets or contracts.
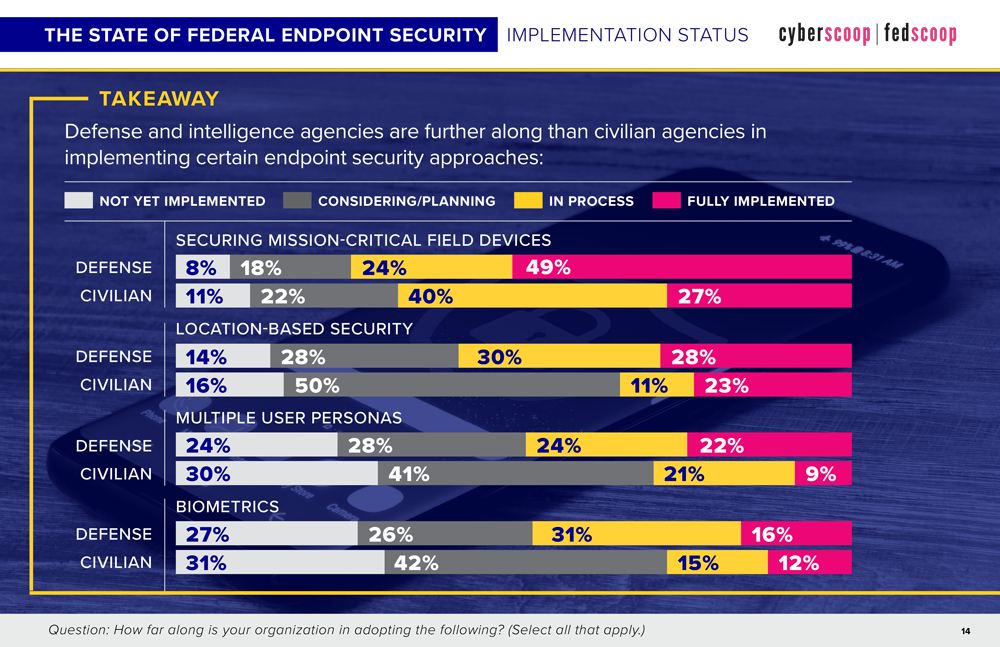
The study found that at least 6 in 10 federal IT/security officials have implemented, or are in the process of implementing, various methods for securing endpoint devices, including:
- Multi-factor authentication – 79%
- Single sign-on – 76%
- Securing endpoint devices – 75%
- Identify management – 73%
- Securing mission-critical field devices – 69%
- Role-based security – 69%
- Remote device management – 67%
- Role-driven secure access – 60%
- Derived credentialing – 59%
Defense / intelligence agencies are outpacing civilian agencies in embracing biometrics and alternative forms of authenticating users to improve endpoint security.
The study also identified the top priorities and concerns IT officials face securing mobile and endpoint devices; the security features and capabilities most important to them in the tools they’re acquiring; and the top challenges agencies face in implement modern endpoint security tools.
Preventing cybersecurity breaches via endpoint devices and improving the time it takes to recover when breaches occur topped the list of mobile security priorities for IT officials over the coming 12-18 months. Securing government-issued devices and guarding against network and endpoint attacks ranked among respondents’ top concerns.
The study, however, also pointed to current and emerging gaps federal IT officials face in addressing endpoint security risks.
One is the growing use of personal mobile devices by federal employees to do their work, but the limited extent to which federal IT department support those devices. More than 90 percent of agency IT officials said their organizations provide secure mobile access for work-issued devices, but less than 20 percent support workers’ personal devices to access most agency systems. However, 40 percent of those same officials voiced concern about the securing personal devices.
Agencies also face a variety of barriers to securing endpoint devices. Budget funding, cumbersome approval processes, the lack of internal expertise and the need for greater guidance on emerging threats and technical support among the most often-cited obstacles.
But the study also suggested that in light of long-standing budget limitations, agencies could take greater advantage of technologies they may already have or own — or is readily available in the commercial market — to improve endpoint security, such modern mobile devices that support biometrics, containerization and derived credentialing.
So, what does this mean for the cybersecurity teams of the future?
Download the Federal Endpoint Security report, “Closing the gaps in federal endpoint security,” for detailed findings and guidance on how agencies are implementing modern endpoint security.
This article was written and produced by FedScoop and underwritten by Samsung.