Military unsure how physical access is handled at more than 100 installations

The Pentagon doesn’t know how military installations are using physical access control systems (PACS) to manage entry because the Army, Navy and Marine Corps don’t track that information.
PACS scan credentials against FBI and other government databases, and after several shootings at military posts, the Department of Defense (DOD) recommended fielding more such systems to address weaknesses.
An Army officer shot 45 people, killing 13, at Fort Hood, Texas, in November 2009. And a Navy contractor shot 16 people, killing 12, at the Navy Yard in Washington, D.C., four years later.
The Defense Manpower Data Center (DMDC) developed the PACS used by the Air Force, Navy, Marine Corps and Defense Logistics Agency (DLA) — called the Defense Biometric Identification System (DBIDS). The Army developed its own system known as Automatic Installation Entry (AIE).
Both systems connect to the Pentagon’s Identity Matching Engine for Security and Analysis (IMESA), which uses government databases to vet a person based on the risk they pose. To date, IMESA has flagged about 42,000 instances of people granted access to DOD installations who subsequently were issued felony warrants.
“Although according to DOD officials DOD has fielded or plans to field PACS that connect to IMESA at all domestic installations, only the Air Force and DLA have monitored PACS use at their installations,” reads a Government Accountability Office report released Thursday. “The Army, the Navy, and the Marine Corps at more than 100 installations have not monitored the use of PACS because, as stated by officials, there is not a requirement to do so.”
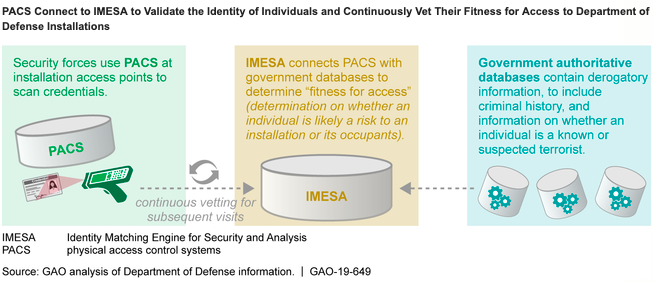
As of February 2019, the Air Force, Navy, Marine Corps and DLA have fielded DBIDS at all 144 of their domestic installations. The Army reported fielding AIE at 35 domestic posts, with plans for 60 more installations by September and any remaining by the end of fiscal 2021. Currently, Army leadership is deciding whether to use DBIDS or AIE at the remaining facilities with plans expected to be finalized this summer.
DMDC intends to improve IMESA by expanding the type of credentials DBIDS can scan to include everything listed in DOD’s 2019 physical security manual. That includes identification cards and driver’s licenses compliant with the REAL ID act of 2005 — eliminating the need for temporary credentials. Veteran health identification card readers are also in the works.
The center is working on connecting additional government databases to IMESA, like the National Crime Information Center’s National Sexual Offender Registry File and Violent Persons File, as well as the Interstate Identification Index, by Sept. 30. DOD’s Automated Biometric Identification System will also be connected to IMESA by 2020.
AIE can already scan ID cards and driver’s licenses, and the Army wants to move the system to the cloud for even quicker fielding.
But without system data, the military can’t evaluate PACS effectiveness or make risk-based decisions to protect personnel and high-value assets, according to the report. Data collected by the Air Force and DLA included PACS use and number of credentials scanned.
GAO further found that system component and installation officials were dissatisfied with how long it took to resolve technical issues with DBIDS.
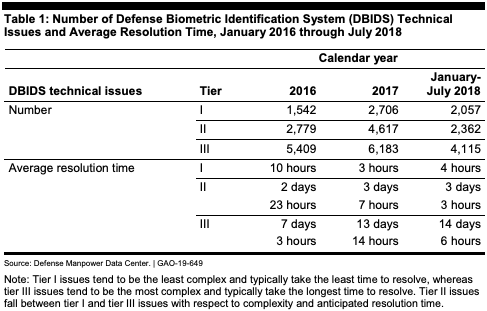
DMDC’s help desk needs to develop DBIDS performance measures and goals to address its underlying operational issues, much like the Army’s help desk did with its system, GAO said. The Army analyzed 646 help desk tickets between October 2017 and February 2018 and pinpointed that site server and handheld device failures were to blame for most technical issues — subsequently updating software and handheld devices at military posts.
DOD, Army, Navy, and Marine Corps officials all agreed with GAO’s recommendations they should require the monitoring of PACS use at all installations and said that it could be done with existing technology without incurring significant additional costs.
GAO assessed DOD access control in accordance with the National Defense Authorization Act for FY 2018. The initial, sensitive report was released in May.





