Federal cyber-incidents were down in 2016 — at least on paper

Federal agencies in 2016 experienced less than half the number of cyber-incidents they did in 2015, according to new Government Accountability Office data — but there’s a catch.
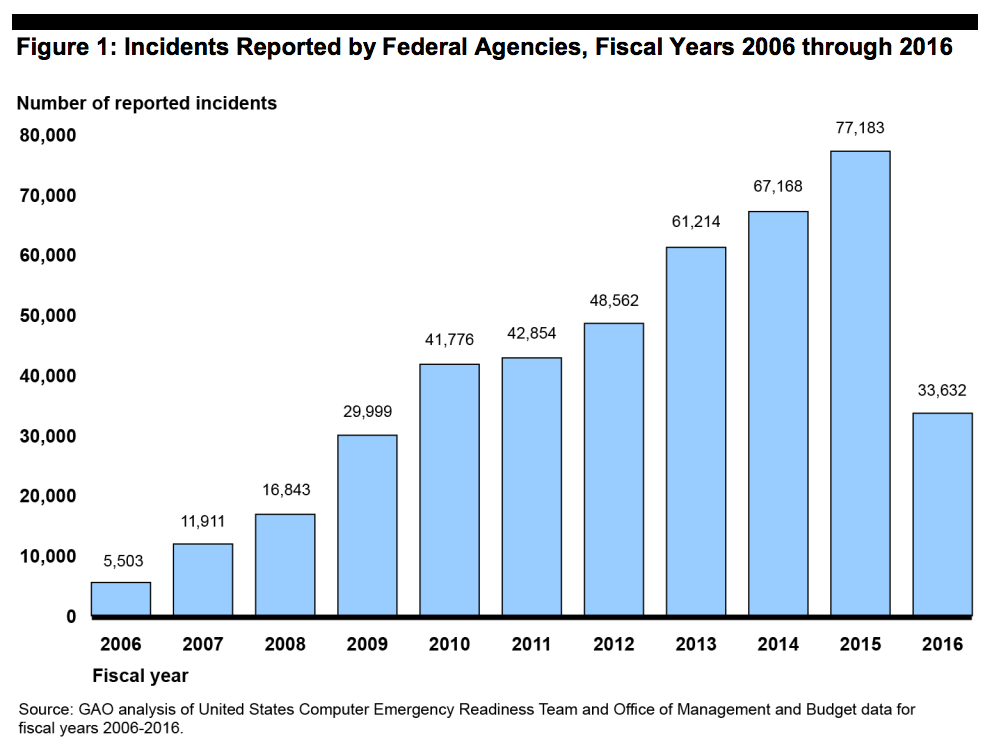
The drop-off from 77,183 agency cyber-incidents reported to the Department of Homeland Security’s U.S. Computer Emergency Readiness Team in fiscal 2015 to 33,632 in fiscal 2016 — a 56 percent decrease — may have as much to do with a change in the reporting requirements in the latest tally as it does with improved cybersecurity defenses.
“An official from DHS’s National Cybersecurity and Communications Integration Center stated that the decrease in reported incidents for fiscal year 2016 was likely due to revised incident reporting requirements that no longer require agencies to report non-cyber incidents or attempted scans or probes of agency networks,” according to a GAO report released Tuesday and presented to the House Committee on Science, Space, and Technology. “The official also cited the expanded use of the National Cybersecurity Protection System to detect or block potentially malicious network traffic entering networks at federal agencies as another possible reason for fewer reported incidents.”
DHS issued those new US-CERT reporting guidelines in 2015; the department is again in the process of revising them, with new guidelines set to take effect April 1 that do not appear to contain the same clause asking agencies to refrain from sharing”non-cyber” breaches of personally identifiable information.
Prior to 2016, the GAO had tracked a constant increase in federal cyber-incidents reported year-over-year — a 1,303 percent increase from 5,503 incidents in 2006 to 2015’s 77,183.
(GAO)
Despite what appears to be progress, the GAO claims in the report that of the 2,500 recommendations it made in recent years aimed at improving federal information security, more than 1,000 of them are still outstanding.
Greg Wilshusen, the report’s author and director of information security issues at the GAO, testified Tuesday before the committee’s Subcommittee on Research and Technology there could be a variety of reasons agencies are so far behind on implementing the recommendations.
“The recommendations in some instances require a longer period of time to actually implement consistently throughout the organization, and that may have one factor,” Wilshusen said. “Another factor is that agencies often will close out a recommendation as implemented when they may have a plan to implement the recommendation and not necessarily take the actions needed to across the enterprise. We often find that when we go back to an agency that has made such indications that they have implemented the ‘recs,’ when we go in and test the systems across the organization, the conditions still exist.”






