- Sponsored
- Sponsored Content
Identity corroboration methods key to reducing fraud, report says

Keeping up with identity verification and fraud detection practices is a growing concern for government agencies as they move more services online. However, traditional methods for corroborating identity are increasingly compromised due to continued breaches of personal data and require a broader approach, a Gartner report says.
The report, “2018 Gartner Market Guide for Identity Proofing and Corroboration,” made publicly available recently by LexisNexis Risk Solutions, recognizes the growing risks of fraud from identity theft and the need for smarter approaches to authenticate users.
Read the full report.
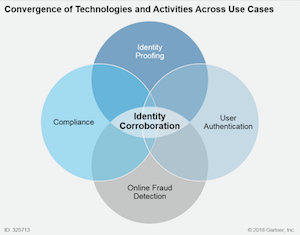
“The lines between online fraud detection, identity proofing, compliance and user authentication use cases are increasingly blurring with regard to the techniques that can be applied to increase trust assurance and better identify malicious or anomalous activity,” the report states.
The report places the practice of identity corroboration at the hub of several inter-related technologies and disciplines needed to assess and assure the trustworthiness of a user’s identity, including identity proofing, user authentication, online fraud detection and compliance.
Altogether, the report defines identity proofing and corroboration as the affirmative and negative signals which yield a net confidence, or level of trust in the identity claim. Affirmative signals include curated credentials, third-party credentials and familiarity signals. Negative signals include anomalies, attack signals and risk signals.
“There are myriad data types and signals that must be corroborated and analyzed in order to achieve a sufficient level of trust in a modern identity proofing and corroboration use case,” the report explains. Already, many organizations in the private sector are turning to providers that can offer identity hub solutions.
The report also lists and assesses 20 vendors that provide various identity hub components. LexisNexis Risk Solutions was cited among the providers as offering the most complete range of tools.
Even though government agencies may not require a full suite of identity corroboration capabilities today, the report cautions that sophisticated attacks are moving down-market, and it recommends a strategic plan to incorporate some of these new technologies.
The Gartner report also touches on some best practices for leaders in security and risk management to apply in identity corroboration, such as:
- Perform an inventory of your current identity proofing methods, and assess the likelihood that the existing methods can be subverted by criminals.
- Include the cost of poor customer experience when evaluating the business case for new investments for identity proofing use cases.
- Prioritize the detection of identity-related attacks at all facets of customer interaction, including both online and offline channels.
- Ensure the identity proofing and substantiation strategy ties into a broader risk management framework encompassing new application assessment, user authentication, fraud detection and prevention, and account management.
- Evaluate the use of an identity hub to enable the orchestration and testing of multiple solutions as the need arises.
Read the full report for more information on how to reduce the risk of fraud and ensure a high level of trust in user identity.
This article was produced by FedScoop for, and sponsored by, LexisNexis Risk Solutions.






