- Sponsored
- Defense
Derived credentials explained, the balance of security and user experience on mobile devices
Two-thirds of government IT users and half of IT managers in a recent FedScoop study ranked single sign-on to all applications on their devices among the top three things that would make their digital experience more productive at work.
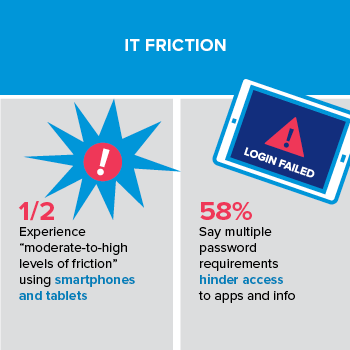
So why is the government struggling to adopt derived credentials — a user-friendly, secure method for adding strong authentication to mobile devices — at a time when agencies and users are also looking for ways to improve productivity and reduce IT friction?
Download the full report.
According to Eugene Liderman, director of product management at VMware, who focuses on security and privacy, derived credentials offer government agencies a reliable, user-friendly and compliant method for adding strong authentication to mobile devices. This approach also gives agency CIOs a proven alternative to costly and cumbersome physical personal identity verification (PIV) card readers often required to access government information systems. With government users looking for a faster, easier and less frustrating mobile experience, derived credentials can provide multi-factor authentication with a fast and seamless user experience.
A new FedScoop report, “Understanding derived credentials for the federal government,” addresses common misconceptions about derived credentials, explains how they work and outlines recommendations for CIOs considering implementing derived credentials in their organizations.
Overcoming misconceptions about derived credentials
Liderman says the federal government faces two main challenges to the adoption of derived credentials: misconceptions around complexity and misunderstanding regarding use and cost.
“A lot of people think of derived credentials as a silver bullet that’s a technological breakthrough that is super complicated,” says Liderman. “In fact, it’s not a new product or a new technology; it’s more of a framework, a procedure, a flow of how you enroll and get a derived credential onto your device and use it. It’s not so different from what we do today, and there is not as much friction to get going with it.”
The National Institute of Standards and Technology (NIST) defines a derived credential as an alternative token to create multi-factor authentication with a mobile device, such as a smartphone or tablet.

Liderman says agencies can leverage this alternative method to provide multi-factor security for mobile devices without smart cards and readers, which are clunky and impractical for mobile devices.
In an attempt to mitigate the need to use smart cards with mobile devices in the government, many agencies simply are not enforcing the use of two-factor authentication on smartphones or mobile devices like tablets, which goes against federal security guidelines. NIST Special Publication 800-157 presents derived credentials as a viable alternative.
In addition to enabling secure mobility for federal defense and civilian organizations, derived credentials also empower managers with control over applications and data, even when they do not own or have control of the devices. Plus, users have the flexibility to access apps and data they need for work, anytime, anyplace, from any devices.
Download the special report for more on understanding and implementing derived credentials in federal defense and civilian agencies.
For more on improving government workforce productivity and security, go to FedScoop’s Public Sector Innovation Priorities series.
This article was produced by FedScoop for, and sponsored by, VMware.






